A proper configuration of Apache Web server may extremely important since it sometimes can prevent certain Web Application Attacks even though the vulnerability is there in the web application. In this post, I’ll describe how to set configure apache to send Security concerned HTTP headers in its response and hide sensitive information from server response headers. In a later post, I’ll describe setting virtual hosts with SSL enabled, request rewriting and redirection.
If you carefully inspect HTTP responses coming from Web Servers from Google or Facebook or any other Securely configured server, you might see several non-HTTP-standard headers inside their response. Some of them are,
X-Frame-Options
X-XSS-Protection
Strict-Transport-Security
X-Content-Type-Options
X-Content-Security-Policy/X-WebKit-CSP
These headers are sent by the web server to trigger browser security mechanisms which browsers use to prevent certain Web Application attacks. You can find more information on these headers at this OWASP page. If not configured manually, these headers are not sent by Apache server and hence browser security mechanisms are not activated.
Example:-
X-Frame-Options header is sent by a server to prevent ClickJacking attacks. When this header is set to DENY browser do not let you display the response inside an Iframe. If this header is not set in the response, the browser does not trigger that protection mechanism. So, letting a page to be displayed inside an iframe make the application vulnerable to clickjacking attacks.
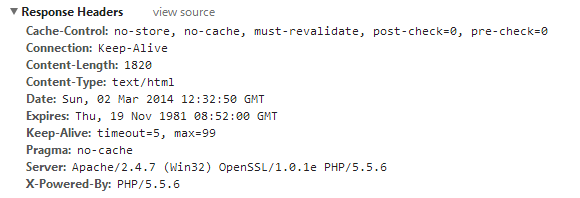
Another important fact is that most people keep their default configurations left, which in turn reveals some important information about their server to attackers. Have a look at the folllowing response.
You can clearly see that above response is coming from an Apache web server with version 2.4.7 and you can see its OpenSSL and PHP versions and on which platform its running (in this case Windows) clearly. An enthusiastic attacker can search online for published vulnerabilities and exploits for above server on the given platform and the software installed on the server, if a matching exploits found, he can easily attack your web server. So, this information should never be revealed and should be hidden or obfuscated.
So what we are going to do is,
- Hide unnecessary headers/information from the server response
- Add aforementioned security headers to the server response
Hide detailed information from server response headers
To mask detailed information from Server header, edit Apache’s /etc/apache2/apache.conf file. Open the file and add the following entries at the end.
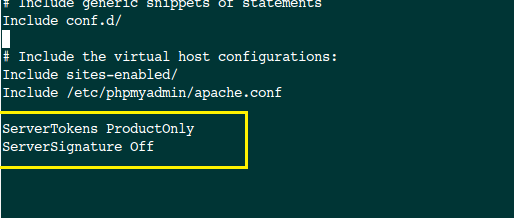
By changing the parameter of ServerTokens, you can mask information in few levels. Following is possible values for ServerTokens parameter.
ServerTokens Full (or not specified) Server sends (e.g.): Server: Apache/2.4.2 (Unix) PHP/4.2.2 MyMod/1.2
ServerTokens ProductOnly Server sends (e.g.): Server: Apache
ServerTokens Major Server sends (e.g.): Server: Apache/2
ServerTokens Minor Server sends (e.g.): Server: Apache/2.4
ServerTokens Minimal Server sends (e.g.): Server: Apache/2.4.2
ServerTokens OS Server sends (e.g.): Server: Apache/2.4.2 (Unix)
After saving the file, if I restart apache server running the command,
sudo service apache2 restart
I can now see that detailed information from the server header is removed and it only displays the server is Apache.

And also we need to hide PHP version which is disclosed by X-Powered-By header. To do that, simple include following line inside /etc/apache2/httpd.conf file.
Header unset X-Powered-By
This command will remove X-Powered-By header from the response and after restarting apache server you can see there is no more PHP version disclosure in the header.
Configuration of Important HTTP Response Headers
Now we need to the server to send Important security headers with the response. You can do this editing very file/etc/apache2/httpd.conf and add the following lines.
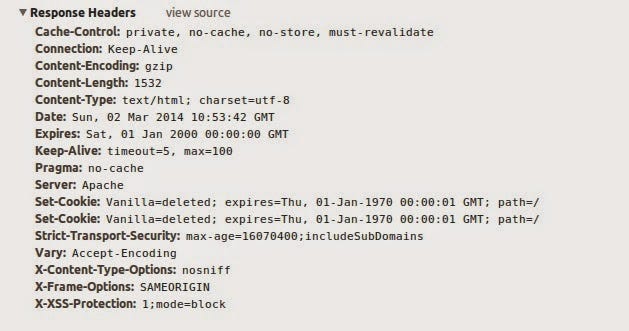
Header set X-Frame-Options SAMEORIGIN
Header set X-XSS-Protection 1;mode=block
Header set X-Content-Type-Options nosniff
In this case, let's consider only the above three headers. Upon this configuration and server restart, you’ll now see these headers are now set in the server response.
These are only a few configurations. Put a comment if there’s any correction or something to be added.
References: