TOR, The Onion Router in long terms, is a world well known Anonymous Network which provides users browse internet ‘Completely’ anonymously. Highlighting the word ‘Completely’ I don’t say that nobody will ever know who you are and what you say on the internet through Tor. I will later describe some situations in which this ‘Completely’ term ‘Completely’ breaks.
However, TOR has been protecting people’s identity from uncovering and letting them express their ideas over the internet anonymously. As the official Tor website (https://www.torproject.org/) says, the main users of this Tor network are Activists, Military and Law enforcement, Media and various other people for their tasks. Besides them people misuse this network to visit banned websites, download sexual content bypassing filters and most importantly, Tor network is now used by Hackers to attack organizations without revealing their identity. The most reason example for the later was the recent Skynet Botnet in which Command and Control Servers (C&C) hidden behind the Tor Network.
How Does TOR Work ?
Tor consists of a network of relay servers which are run by volunteers all over the world. When a user connects to the Tor network using a Tor client/Tor-enabled browser, a path is created from the user to the destination server to which the user needs to connect. This path consists of three relay servers called Entry Node, Middle Node and Exit Node.
All the requests the sender sends to the destination through the Tor network are relayed through this pre-built path and the responses from the destination return back to the sender through the same path. All the data going through the Tor network is completely encrypted such that nobody who intercepts the communication has no clue who the sender is. But, if one sniffs outgoing link from the exit node can capture the data transmitted both sides, but anonymity is still secured. I will later explain how this protection happens.

When you download Tor from the website, you can run Tor as a local SOCKS proxy in your computer. When your browser is configured to use that local SOCKS proxy, you can browse the internet with that browser through the tor network. You can configure many applications to use this SOCKS proxy and use them through Tor network, these applications include web browsers, download manager software, BitTorrent clients, etc.
Bypassing Firewalls and Filtering mechanisms
When you are connected to a server via Tor network, your firewall or any filtering device only sees you are connected to a node of the Anonymous network, not to the actual server you are communicating with. And with the data encrypted, these filtering mechanisms cannot inspect inside the packets and cannot interpret the actual content. So these data is slipped through firewalls and filtering mechanisms.
How Tor Protects Anonymity
Tor is an implementation of Onion Routing which provides Multi-Layer encryption for users’ data and relays through a network of Onion Routers. So what is onion routing?
Say a user is connected to a destination server through a network of Onion Routers (or Relays). The data user sends to the destination server is encrypted in multiple layers so that each layer can only be decrypted by one onion router in the network. So if the user is connected to a destination through 4 Onion routers, the data sent is encrypted in 4 layers. In Tor Network, a user is connected to 3 nodes in the Tor network. Following diagram is taken from Wikipedia which clearly show how data is encrypted in 3 layers.
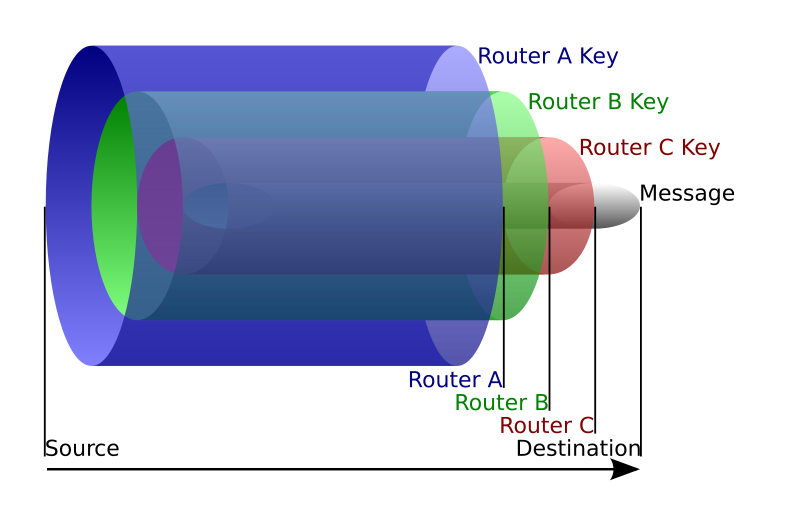
When a user connects using Tor as a proxy server, Tor finds 3 Nodes (Entry node, Middle Node, and Exit Node) in the anonymous network. During this discovery, Tor also generates 3 separate shared secret keys (symmetric keys) with each node using the Diffie-Hellman Key Exchange. Any router among these three has no idea about what other two’s keys are. Only the sender has the three keys so that it can encrypt the data he sends in 3 layers. As the above diagram shows, once this 3-layer-encrypted data is sent through these three nodes, Entry node decrypts the first layer of the encryption using his shared secret key and discovers where to relay the data. But it has no capability to find out the actual data because it is encrypted using a key which it does not have. Then the 2-layer-encrypted data coming from the Entry Node is relayed to the Middle Node. Then it decrypts the next layer of encryption using its shared secret key as above described. And the decrypted data is relayed to the Exit node. The data coming to the Exit Node is only encrypted in One layer. So, when it is decrypted using the Exit Node’s shared secret key, the actual plain text data is revealed. Then this actual data is sent in plain text to the destination server.
So we have a clear security threat with these Exit nodes. If an Exit node is compromised or an exit node is run by a malicious party, the attacker has the capability to sniff all the traffic which comes out from the Exit node and capture sensitive information such as user credentials and bank information. So, for the maximum level of security, users are advised to visit websites using a secured HTTPS connection. Then the outgoing traffic from the exit node is also encrypted using a shared key which only the sender and the destination knows, the attacker cannot identify the data.
I found an amazingly nice and clear graphics elaboration on how Tor works with and without HTTPS. This is created by Electronics Frontier Foundation. You can visit the original article here.

